Information management: the operating system provides
a certain number of indicators that can be used to diagnose the correct
operation of the machine.
File System:
Even though hard drives can be
very small, they still contain millions of bits and therefore need to be
organized so that information can be located. This is the purpose of the file
system.
|
Operation system
|
File
system types supported
|
|
Dos
|
FAT16
|
|
Windows 95
|
FAT16
|
|
Windows 95 OSR2
|
FAT16, FAT32
|
|
Windows 98
|
FAT16, FAT32
|
|
Windows NT4
|
FAT, NTFS (version 4)
|
|
Windows 2000/XP
|
FAT, FAT16, FAT32, NTFS (versions
4 and 5)
|
|
Linux
|
Ext2, Ext3, ReiserFS, Linux Swap(,
FAT16, FAT32, NTFS)
|
|
MacOS
|
HFS (Hierarchical File System),
MFS (Macintosh File System)
|
|
OS/2
|
HPFS (High Performance File
System)
|
|
SGI IRIX
|
XFS
|
|
FreeBSD, OpenBSD
|
UFS (Unix File System)
|
|
Sun Solaris
|
UFS (Unix File System)
|
|
IBM AIX
|
JFS (Journaled File System)
|
File Attributes:-
·
A file's attributes vary from one OS to another but typically consist of
these:
- Name.
- Identifier. This unique tag, usually a number, identifies the file within the file system; it is the non-human-readable name for the file.
- Type.
- Location. This information is a pointer to a device and to the location of the file on that device.
- Size. The current size of the file (in bytes, words, or blocks) and possibly the maximum allowed size are included in this attribute.
- Protection. Access-control information determines who can do reading, writing, executing, and so on.
- Time, date, and user identification. This information may be kept for creation, last modification, and last use.
· The information
about all files is kept in the directory structure, which also resides on
secondary storage. Typically, a directory entry consists of the file's name and
its unique identifier.
File
Access Mechanisms
File access mechanism refers to the
manner in which the records of a file may be accessed. There are several ways
to access files
- Sequential access
- Direct/Random access
- Indexed sequential access
Sequential
access
A sequential access is that in which
the records are accessed in some sequence i.e the information in the file is
processed in order, one record after the other. This access method is the most
primitive one. Example: Compilers usually access files in this fashion.
Direct/Random
access
- Random access file organization provides, accessing the records directly.
- Each record has its own address on the file with by the help of which it can be directly accessed for reading or writing.
- The records need not be in any sequence within the file and they need not be in adjacent locations on the storage medium.
Indexed
sequential access
- This mechanism is built up on base of sequential access.
- An index is created for each file which contains pointers to various blocks.
- Index is searched sequentially and its pointer is used to access the file directly.
Directory Structure:
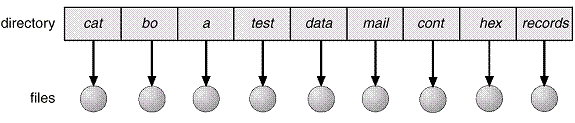
Single-Level
Directory
A
single directory for all users.
Naming
problem
Grouping
problem
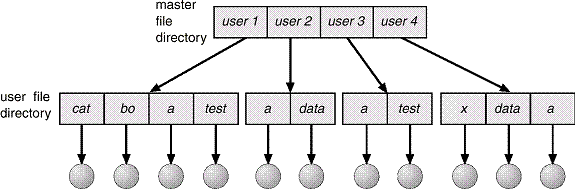
Two-Level
Directory
Separate
directory for each user.
•Path
name
•Can
have the same file name for different user
•Efficient
searching
•No
grouping capability
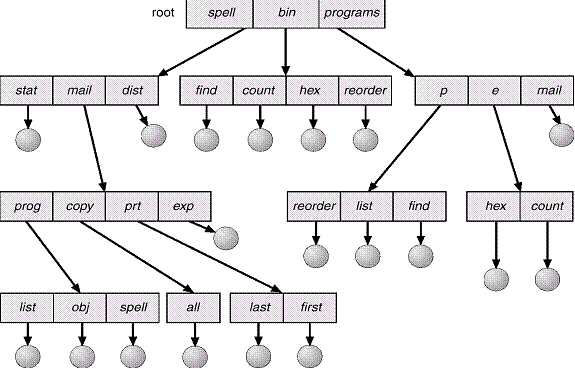
Tree-Structured
Directories
Efficient
searching
Grouping
Capability
Current
directory (working directory)
1.cd
/spell/mail / prog
2.
type list
3.
Absolute or relative path name
4.
Creating a new file is done in current directory.
5.
Delete a file
rm
<file-name>
Creating
a new subdirectory is done in current directory.
mkdir
<dir-name>
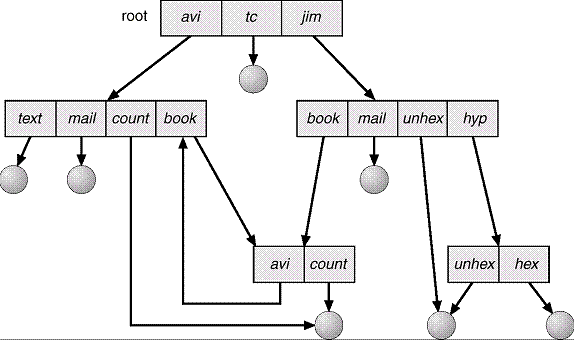
Acyclic-Graph
Directories
Have
shared subdirectories and files.
Two
different names (aliasing)
If dict
deletes list _ dangling pointer.
Solutions:
- Back pointers, so we can delete all pointers.
Variable
size records a problem.
1. Back pointers using a daisy chain organization.
2. Entry-hold-count solution.
General
Graph Directory
Goals
of Protection
- Obviously to prevent malicious misuse of the system by users or programs. See chapter 15 for a more thorough coverage of this goal.
- To ensure that each shared resource is used only in accordance with system policies, which may be set either by system designers or by system administrators.
- To ensure that errant programs cause the minimal amount of damage possible.
- Note that protection systems only provide the mechanisms for enforcing policies and ensuring reliable systems. It is up to administrators and users to implement those mechanisms effectively.
Principles
of Protection
- The principle of least privilege dictates that programs, users, and systems be given just enough privileges to perform their tasks.
- This ensures that failures do the least amount of harm and allow the least of harm to be done.
- For example, if a program needs special privileges to perform a task, it is better to make it a SGID program with group ownership of "network" or "backup" or some other pseudo group, rather than SUID with root ownership. This limits the amount of damage that can occur if something goes wrong.
- Typically each user is given their own account, and has only enough privilege to modify their own files.
- The root account should not be used for normal day to day activities - The System Administrator should also have an ordinary account, and reserve use of the root account for only those tasks which need the root privileges
Domain
of Protection
- A computer can be viewed as a collection of processes and objects ( both HW & SW ).
- The need to know principle states that a process should only have access to those objects it needs to accomplish its task, and furthermore only in the modes for which it needs access and only during the time frame when it needs access.
- The modes available for a particular object may depend upon its type.
Consistency Semantics
- Consistency Semantics deals with the consistency between the views of shared files on a networked system
Authentication:
Operating system (OS) authentication is a method for identifying an
individual user with credentials supplied by the operating system of the user's
computer. These credentials can be the OS password or can include digital
certificates in the user's computer. Operating Systems generally
identifies/authenticates users using following three ways:
·
Username / Password - User need to enter
a registered username and password with Operating system to login into the
system.
·
User card/key - User need to punch card
in card slot, or enter key generated by key generator in option provided by
operating system to login into the system.
·
User attribute - fingerprint/ eye retina
pattern/ signature - User need to pass his/her attribute via designated
input device used by operating system to login into the system.
Program
Threats
Operating system's processes and
kernel do the designated task as instructed. If a user program made these
process do malicious tasks then it is known as Program Threats. One of the
common example of program threat is a program installed in a computer which can
store and send user credentials via network to some hacker. Following is the
list of some well known program threats.
- Trojan Horse - Such program traps user login credentials and stores them to send to malicious user who can later on login to computer and can access system resources.
- Trap Door - If a program which is designed to work as required, have a security hole in its code and perform illegal action without knowledge of user then it is called to have a trap door.
- Logic Bomb - Logic bomb is a situation when a program misbehaves only when certain conditions met otherwise it works as a genuine program. It is harder to detect.
- Virus - Virus as name suggest can replicate themselves on computer system .They are highly dangerous and can modify/delete user files, crash systems. A virus is generatlly a small code embedded in a program. As user accesses the program, the virus starts getting embedded in other files/ programs and can make system unusable for user.
System
Threats
System threats refers to misuse of
system services and network connections to put user in trouble. System threats
can be used to launch program threats on a complete network called as program
attack. System threats creates such an environment that operating system
resources/ user files are mis-used. Following is the list of some well known
system threats.
- Worm -Worm is a process which can choked down a system performance by using system resources to extreme levels.A Worm process generates its multiple copies where each copy uses system resources, prevents all other processes to get required resources. Worms processes can even shut down an entire network.
- Port Scanning - Port scanning is a mechanism or means by which a hacker can detects system vulnerabilities to make an attack on the system.
- Denial of Service - Denial of service attacks normally prevents user to make legitimate use of the system. For example user may not be able to use internet if denial of service attacks browser's content settings.
Encryption:
Filesystem-level encryption,
often called file/folder encryption, is a
form of disk encryption where
individual files or directories are encrypted
by the file
system itself. This is in contrast to full disk encryption where the
entire partition or disk, in which the file system resides, is encrypted.
The advantages of filesystem-level
encryption include:
- flexible file-based key management, so that each file can be and usually is encrypted with a separate encryption key
- individual management of encrypted files e.g. incremental backups of the individual changed files even in encrypted form, rather than backup of the entire encrypted volume[clarification needed]
- access control can be enforced through the use of public-key cryptography, and

No comments:
Post a Comment